Configuring Pega Robot Manager to support OAuth 2.0 with SAML bearer
Allow Pega Robot Manager users to authenticate through OAuth 2.0 with SAML bearer by importing the token-signing certificate from the Security Token Service (STS) and configuring the client registration details in Robot Manager.
The STS is an Internet Information Services web service that serves as a minimal version of Active Directory Federation Services. The STS authenticates Pega Robot Studio and Pega Robot Runtime with Robot Manager by using the domain user credentials of the user’s Windows session.
Uploading the token-signing certificate to your application
Create a keystore that stores the STS token-signing certificate for verifying the identity of Pega Robot Manager users.
- In Dev Studio, click .
- Provide a keystore name and description, and then click Create and open.
- On the Main tab, in the Keystore location field, press the Down Arrow key and select Upload file.
- In the Keystore file name section, click
Upload file and then upload the
.pfxor.jkscertificate that you obtained from your Security Token Service provider. - Specify the type of keystore that you uploaded.
- Provide the password for the keystore.See the following figure for reference:
Uploading a keystore file to Pega Platform 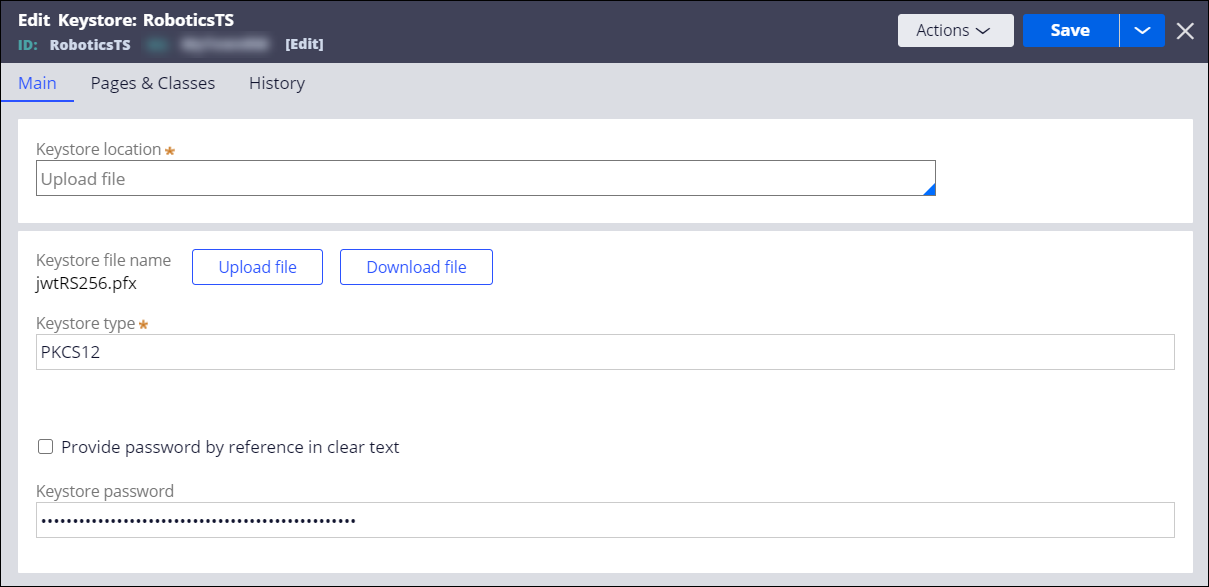
- Confirm your configuration by clicking Save.
Configuring the identity mapping
Map the truststore for the token-signing certificate and specify the method to use to identify Pega Robot Manager users.
The truststore is the rule that stores the certificate.- In Dev Studio, click .
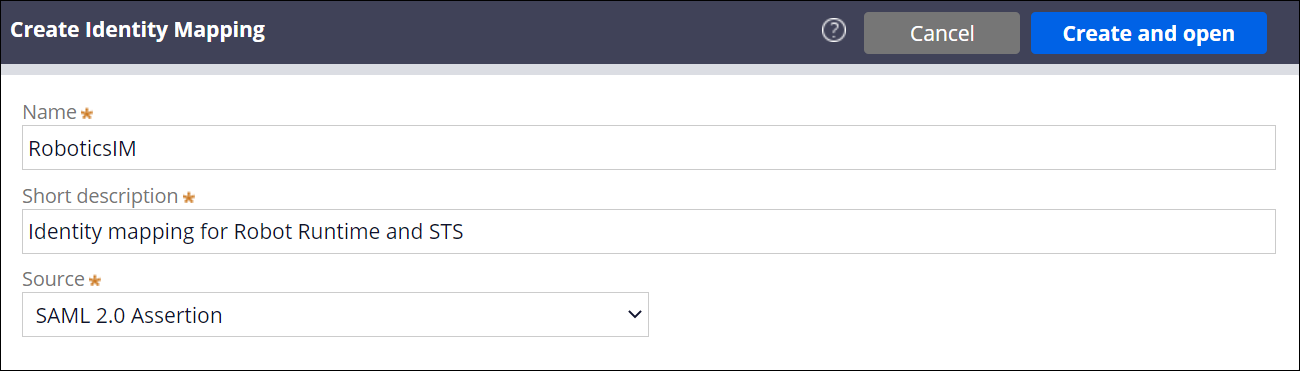
- In the Instances of Identity Mapping section, click Create.
- Provide the details for the new instance of identity mapping:
- Specify the identity mapping name.
- Provide a meaningful short description.
- In the source field, select SAML 2.0 Assertion.
- Click Create and open.
- Configure the identity mapping details:
- In the Truststore field, reference the keystore rule that stores the STS token-signing certificate.
- In the Map operator ID from field, select Attribute or Datapage reference.
- Set the attribute reference by entering {UPN} in
the {attribute name} or D_pageName.propertyName
field.You can reference other attributes, such as the email address, depending on the Security Token Service payload. See the following figure for reference:
Identity mapping details 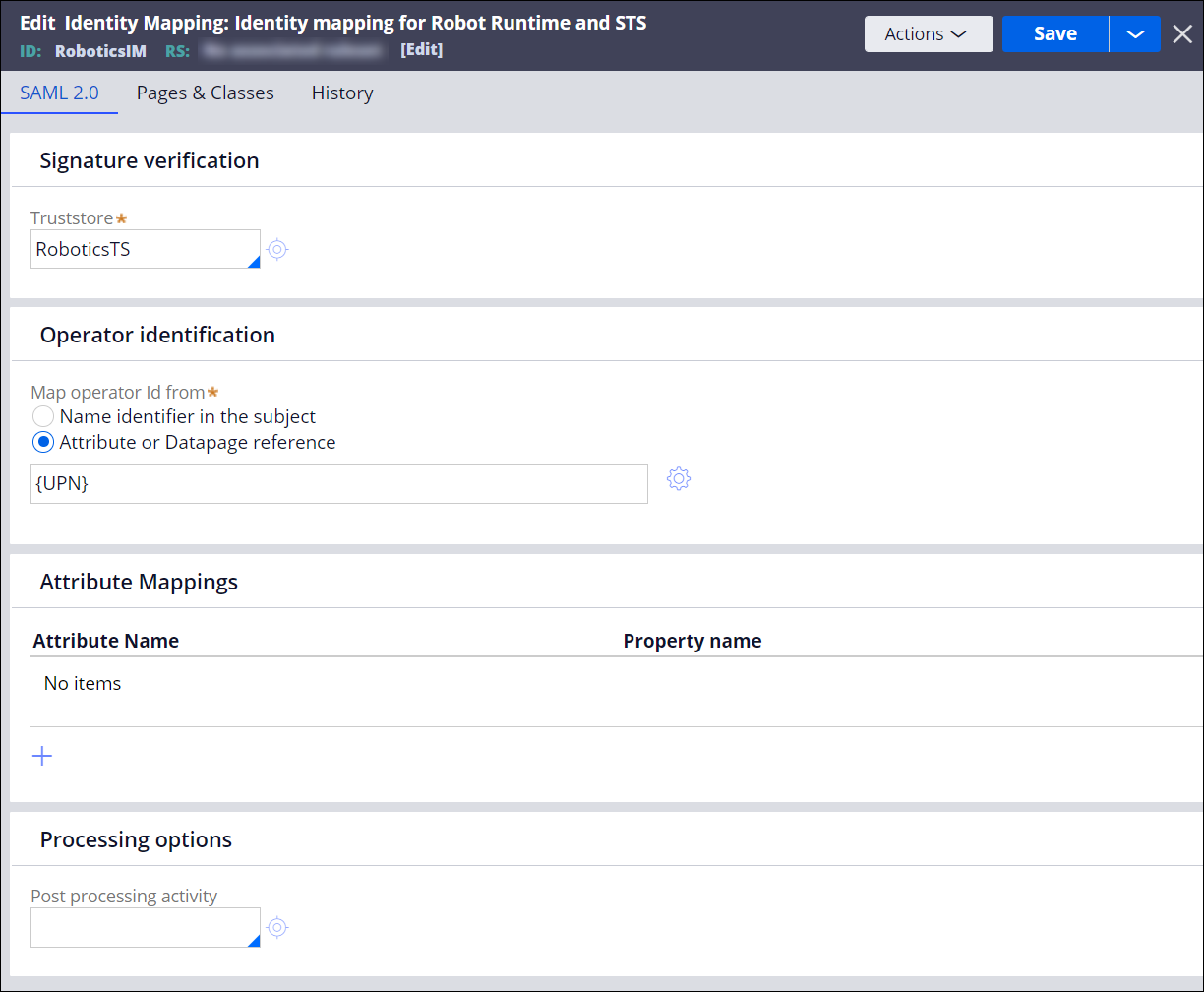
- Confirm your settings by clicking Save.
Configuring the client registration
Create an OAuth 2.0 client registration to allow Pega Robot Runtime to securely access Pega Robot Manager over HTTPS.
- In Dev Studio, click .
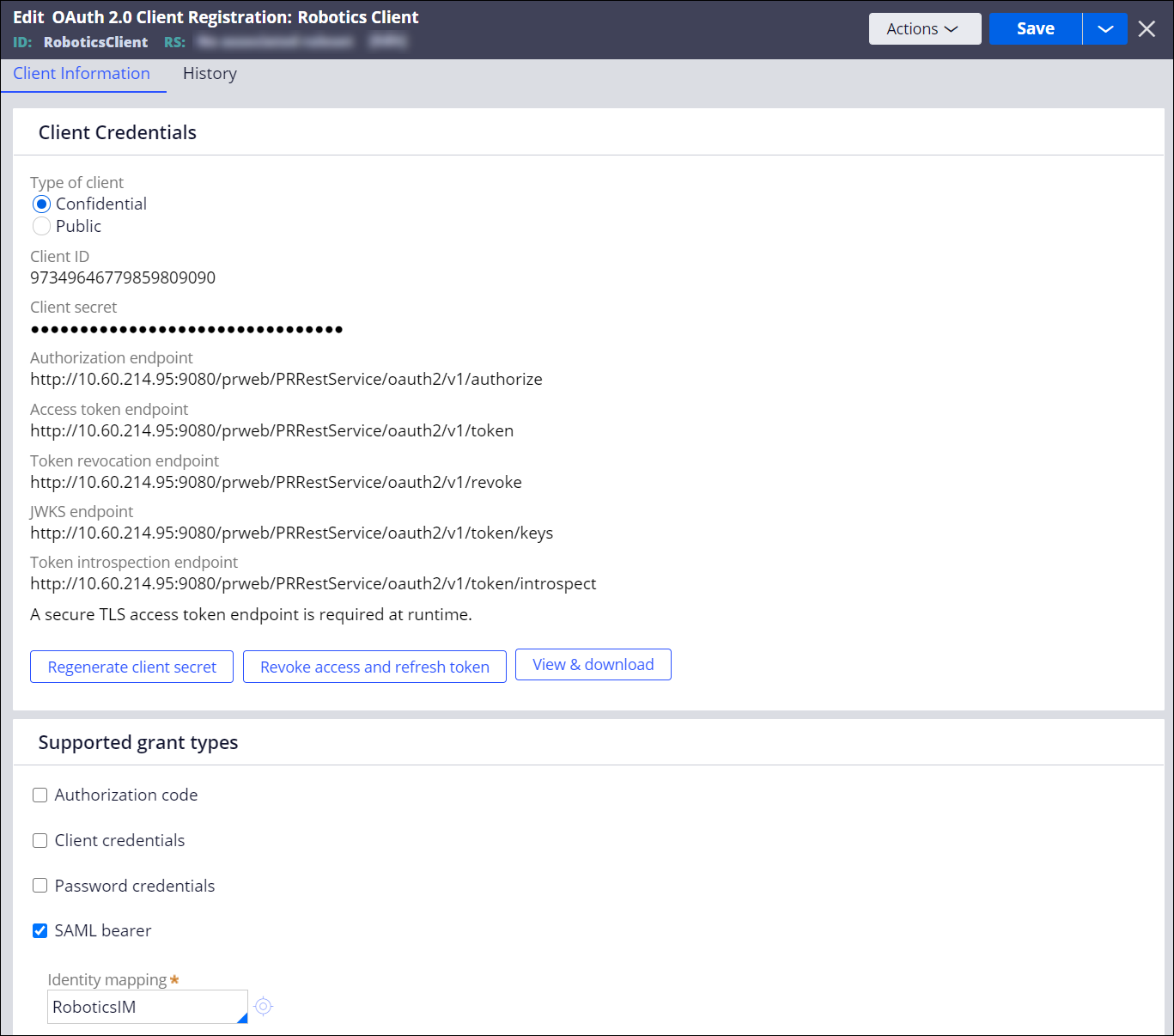
- In the Instances of OAuth 2.0 Client Registration section, click Create.
- Provide the details for the new instance of OAuth 2.0 Client
Registration:
- Specify the identity mapping name.
- Provide a meaningful short description.
- Click Create and open.
- Configure the identity mapping details:
- Ensure that the Type of client field is set to Confidential.
- In the Supported grant types section, select SAML bearer.
- In the Identity mapping field for the SAML bearer option, select the mapping between the Security Token Service and Pega Robot Runtime that you just configured.
- Clear the check boxes for all other supported grant types.
- Save the client ID and the client secret:
- In the Client credentials section, click View & download.
- In the View & download window, click Download credentials.
- Save the
RoboticsClient_ClientCredentials.txtfile in a secure location.
- Confirm your settings by clicking Save.
Previous topic Obtaining the token signing certificate for authenticating Pega Robot Manager users Next topic Adding a relying party